Moria is a relatively new boot2root VM created by Abatchy, and is considered an “intermediate to hard” level challenge. I wasn’t sure I was up for it since I’ve only been doing this for a few months, but much to my delight I conquered this VM and learned a lot in the process. This experience will certainly help as I prepare for the OSCP certification.
While Abatchy says, “No LOTR knowledge is required ;),” I found that my LOTR knowledge came in quite handy.
Getting Started
My setup:
- MacBook running MacOS (Sierra)
- VMWare Fusion running:
- Kali Linux (latest)
- Moria VM
Once the VM was downloaded and running in VMWare, I started through various enumeration techniques that I typically go through when starting to penetration test a box. I’ll omit the irrelevant ones in this write-up.
Enumeration
Netdiscover
This tool revealed the IP of this machine on my network:
192.168.0.131
nmap
I used nmap -v -sS -A -T4 192.168.0.131
and nmap –sS –sV -O 192.168.0.131
PORT STATE SERVICE
21/tcp open ftp vsftpd 2.0.8 or later
22/tcp open ssh OpenSSH 6.6.1 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
MAC Address: 00:0C:29:E8:75:4F (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
So HTTP, FTP, and SSH were running. I started by checking out HTTP and visiting http://192.168.0.131 in a web browser. Here’s what I got:
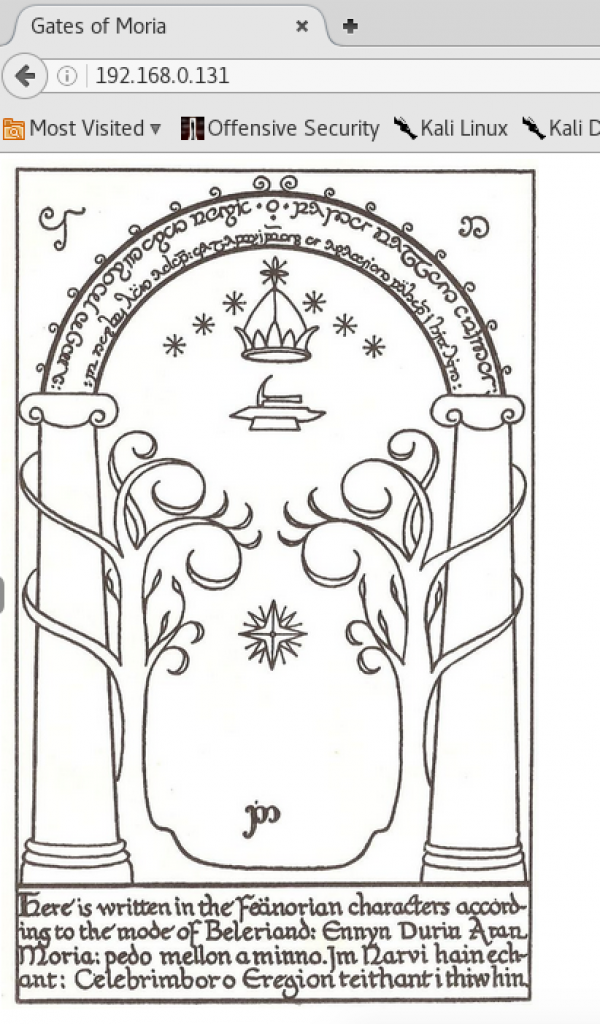
The image of the West Door of Moria is from LOTR. This door was a trick door in the book and movies, and it required some “outside the box” thinking in order to gain entry. I remembered this from the books, and re-familiarized myself with the details via a Google search:
From http://tolkiengateway.net/wiki/Doors_of_Durin:
“On 13 January 3019 the Fellowship of the Ring entered Moria through the Doors,[5] but initially Gandalf could not find out the password to open them. Merry Brandybuck unknowingly gave Gandalf the answer by asking, “What does it mean by speak, friend, and enter?” When Gandalf realized that the correct translation was “Say friend and enter” he sprang up, laughed, and said “Mellon”, which means “friend” in Sindarin, and the Doors opened. Shortly thereafter, the Watcher in the Water attacked the Fellowship and shut the Doors behind them.[1]”
Good info that might come in handy later 😉
dirb
Running dirb led to the discovery of a directory at http://192.168.0.131/w/. It contained a link to /h/, and so on. Traversing down the links led to:
http://192.168.0.131/w/h/i/s/p/e/r/the_abyss/
The page said “Knock knock”
Was this a reference to port knocking? I thought that might be worth checking out later if I could find more info about a sequence.
At this time I was unable to find much more to work with related to the website and HTTP. The usual nikto and other apache/web-related stuff didn’t turn much up. I turned to FTP.
ftp
Trying to connect via FTP turned up some interesting info:
220 Welcome Balrog!
Clearly, the Lord of the Rings theme was running deep. I wondered if the password would be “mellon,” since that was what got the LOTR party into the gates of Moria. I couldn’t get that to work, and I wasn’t sure about a username.
Revisiting the website
Poking around the website some more, I DISCOVERED SOMETHING IMPORTANT!!!
When I browsed to http://192.168.0.131/w/h/i/s/p/e/r/the_abyss/
It gave me something different the next time. I found that a different quote would appear with each page load. I kept refreshing and collected all of the following:
Knock Knock
Is this the end?
Too loud!
Dain:”Is that human deaf? Why is it not listening?”
Nain:”Will the human get the message?”
Is this the end?
“We will die here..”
Ori:”Will anyone hear us?”
Nain:”Will the human get the message?”
Telchar to Thrain:”That human is slow, don’t give up yet”
Maeglin:”The Balrog is not around, hurry!”
Balin: “Be quiet, the Balrog will hear you!”
Oin:”Stop knocking!”
“Eru! Save us!”
A couple of weeks passed at this point, as I went out of town and had other things going on, but it gave me an opportunity to think about Moria and to come back with a fresh perspective.
ssh
Tried a bunch of other things, but finally tried doing SSH to the server and was prompted for a login.
Based on the FTP connection saying “Welcome Balrog!” I assumed that Balrog was a username. I also assumed that Mellon was the password knowing what I know about the LOTR story. Lastly, I realized I probably needed to try various capitalizations.
Using the login combo of Balrog / Mellon I got this:
Wrong gate? OK. I went back to try FTP with the Balrog/Mellon auth combo and got in:
Silly me. The username was right there in front of me when I had been trying FTP before. Nothing in the directory I logged into turned up, but I was able to cd .. up to /
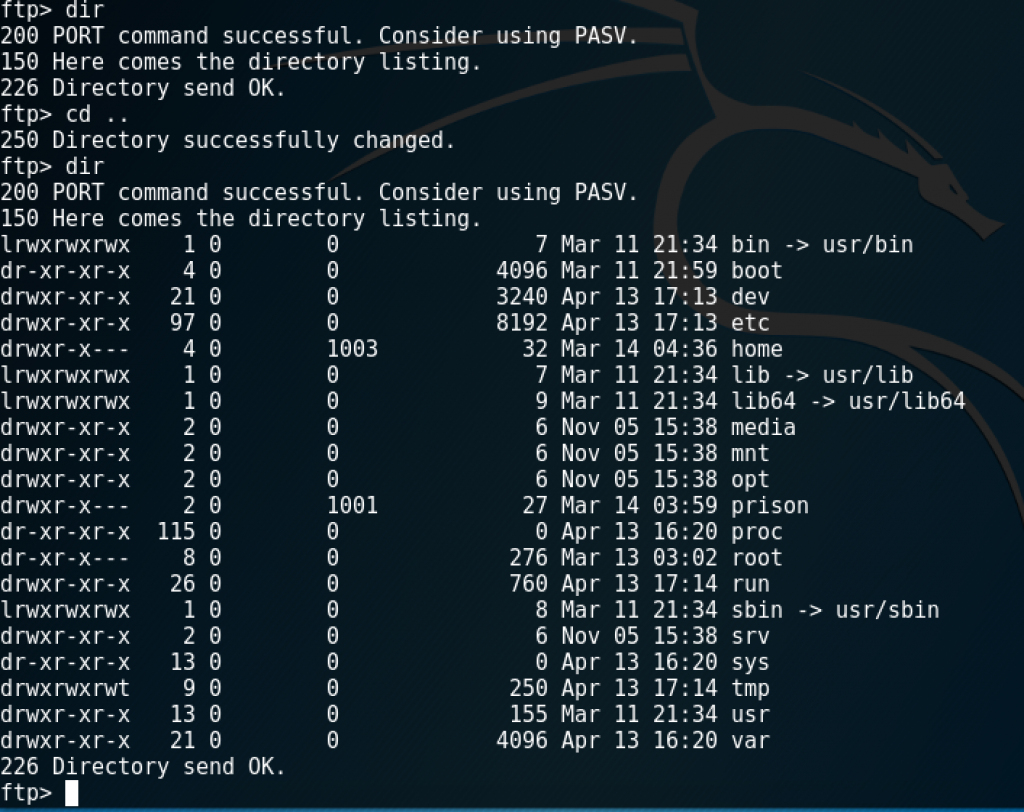
I could go many places with basic dir navigation, but much was not allowed. For example, could get into /etc but not look at passwd. I couldn’t find anywhere that I could upload anything, and none of the important system files you’d typically check were allowed to be viewed.
I went to /var/www/html and found a directory that dirb would never have discovered:

Viewing that page in my web browser showed a handy table of what appeared to be hashes:
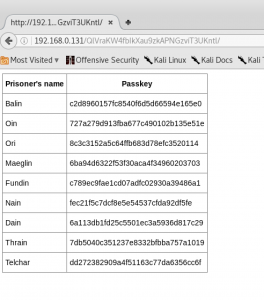 Hashes
Hashes
I set off to see what those passkeys could do. They did’t seem to work as-is for SSH or FTP, so I knew they’d need to be operated on somehow.
hash-identifier said they were likely MD5 hashes:
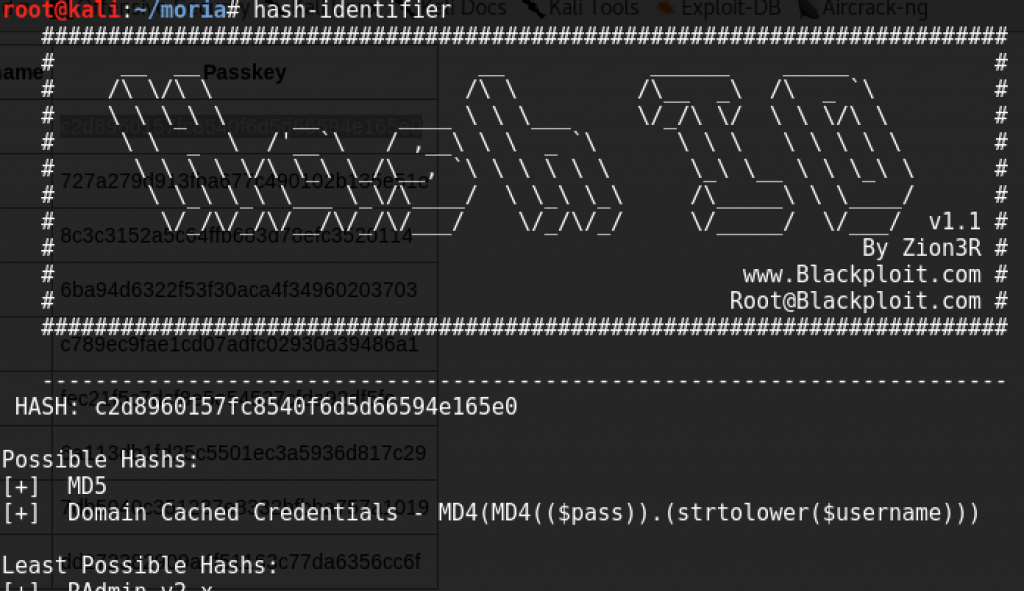
Without a salt I wasn’t sure how I’d use that information.
I tried various things with Hashcat and John the Ripper, but had no luck. I was stumped for a while until I looked under the hood at the source code of that page at http://192.168.0.131/QlVraKW4fbIkXau9zkAPNGzviT3UKntl/
Note: Looking at the HTML source code is something I always forget to do, and it has bitten me more than once!
At the bottom of the source code I found what appeared to be the salts:
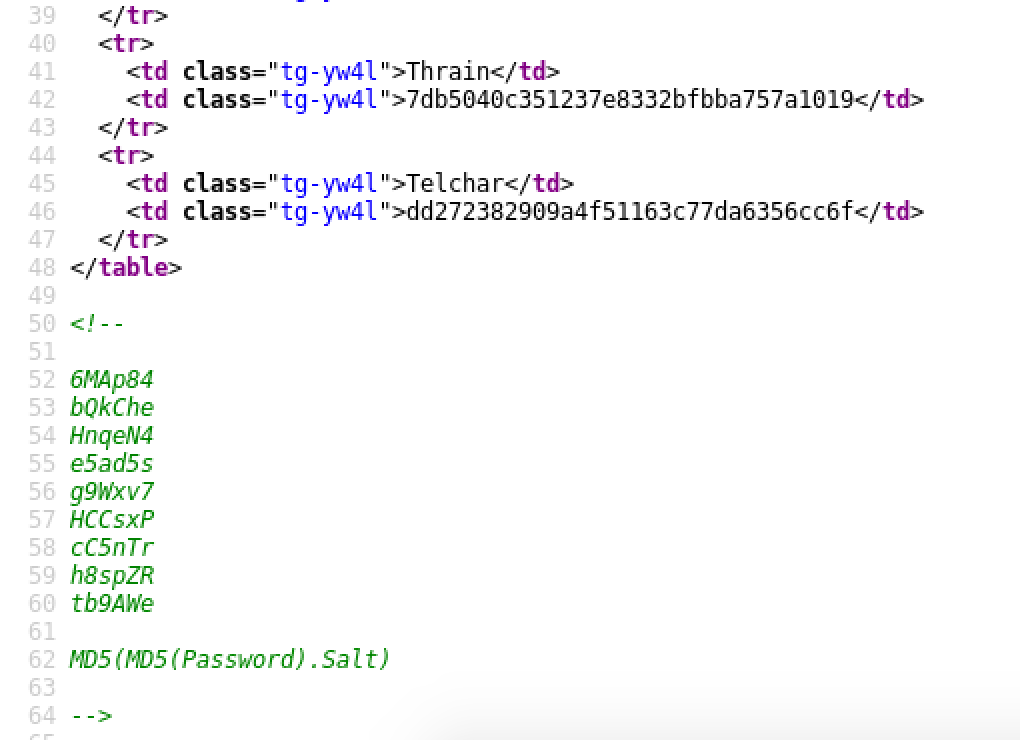
So I had the salts for those MD5 hashes, and I had what looked like the format for using them:
MD5(MD5(Password).Salt)
Cracking
This next part took me a lot of reading and learning, as I’d never really run into this before in my rather limited experience, and I had only a basic knowledge of Hashcat and John the Ripper. While it took some time, it turned out to be a great opportunity to learn.
Ultimately, based on what I had read in various seedy places of the Internet’s underbelly, I created a file called hashes.txt with these contents, based on the HTML chart found above, and added the salts to each line (after the $) respectively:
Balin:c2d8960157fc8540f6d5d66594e165e0$6MAp84
Oin:727a279d913fba677c490102b135e51e$bQkChe
Ori:8c3c3152a5c64ffb683d78efc3520114$HnqeN4
Maeglin:6ba94d6322f53f30aca4f34960203703$e5ad5s
Fundin:c789ec9fae1cd07adfc02930a39486a1$g9Wxv7
Nain:fec21f5c7dcf8e5e54537cfda92df5fe$HCCsxP$HCCsxP
Dain:6a113db1fd25c5501ec3a5936d817c29$cC5nTr
Thrain:7db5040c351237e8332bfbba757a1019$h8spZR
Telchar:dd272382909a4f51163c77da6356cc6f$tb9AWe
I still needed to figure out the right format for running through John the Ripper though, so more research was needed. I turned to these places:
http://pentestmonkey.net/cheat-sheet/john-the-ripper-hash-formats – not much help here.
https://github.com/piyushcse29/john-the-ripper/blob/master/doc/DYNAMIC – found the solution here.
Based on the chart on the documentation page for DYNAMIC, the format mentioned in the source code would work with this:
dynamic_6 | md5(md5($p).$s)
I next tried that on the hashes.txt file:
root@kali:~/moria# john –format=dynamic_6 hashes.txt
Using default input encoding: UTF-8
Loaded 9 password hashes with 9 different salts (dynamic_6 [md5(md5($p).$s) 128/128 AVX 4×3])
Press ‘q’ or Ctrl-C to abort, almost any other key for status
magic (Telchar)
abcdef (Dain)
spanky (Ori)
fuckoff (Maeglin)
flower (Balin)
rainbow (Oin)
darkness (Thrain)
hunter2 (Fundin)
SUCCESS!
I had a list of passwords for each user. Only one of these worked for logging in via SSH, and that was Ori’s account.
Bash Shell Obtained
Got a Bash shell with Ori’s login via SSH:
-bash-4.2$
-bash-4.2$ ls -al
total 8
drwx—— 3 Ori notBalrog 55 Mar 12 22:57 .
drwxr-x—. 4 root notBalrog 32 Mar 14 00:36 ..
-rw——- 1 Ori notBalrog 1 Mar 14 00:12 .bash_history
-rw-r–r– 1 root root 225 Mar 13 23:53 poem.txt
drwx—— 2 Ori notBalrog 57 Mar 12 22:57 .ssh
Starting in Ori’s home directory, I checked out the .ssh directory to see what might be relevant.
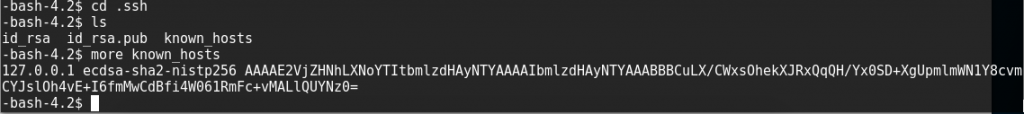
It looked like Ori had logged into localhost before, since it showed up as a known_host. Why would he be doing that unless he needed to log in as someone else? Perhaps as root?
root Obtained – All That is Gold Does Not Glitter
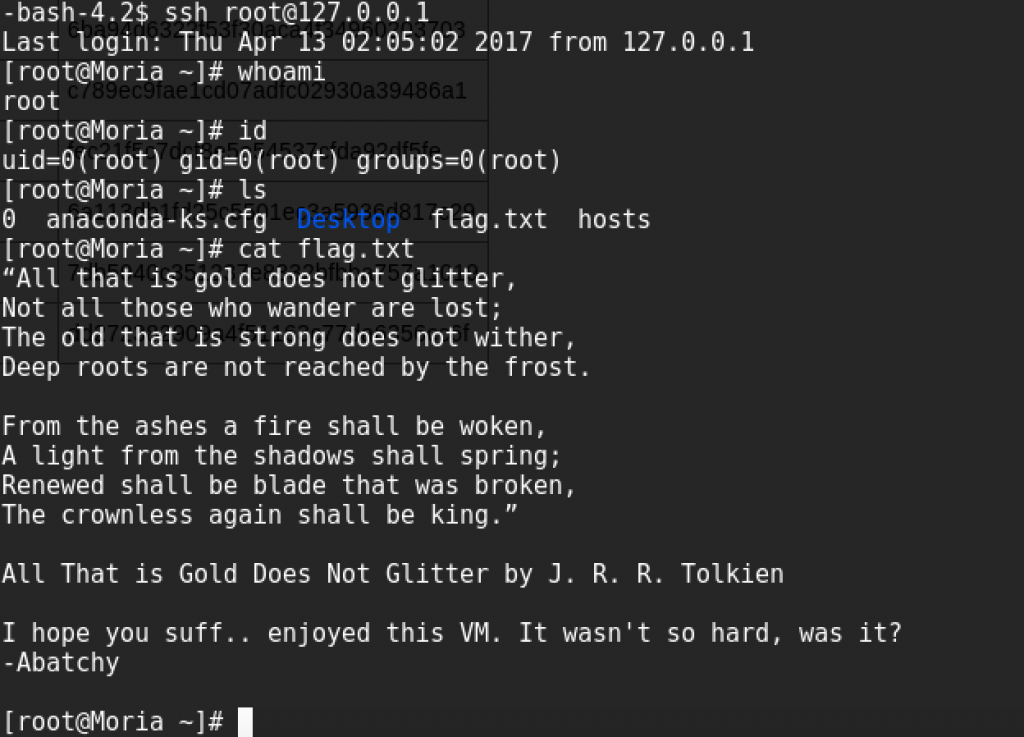
Huh…well that last part was easier than I thought it might be. Thanks to Abatchy for providing this challenge. I learned a lot!

Be First to Comment