About a year ago, Mozilla added “captive portal” support to Firefox in an attempt to enhance usability when connecting to free WiFi portals, such as at an airport or a hotel. You have probably interacted with captive portals in the past, and if you are a Firefox user, you may have wondered why you had to open Chrome or IE or Safari to be able to log into the WiFi system, as you could only get the “Sign In” page to pop up in one of those browsers before getting access to the full Internet.
Firefox added support for these “Sign In” pages about a year ago, so that you don’t need to use a (shudder) different browser. That is all well and good, except for when it comes to using Burp Suite as a proxy for Firefox. If you are a pentester, you are probably used using Firefox (especially on Kali Linux) for your traffic proxying through Burp, as they make it easier than any other browser to set up and disable the proxy.
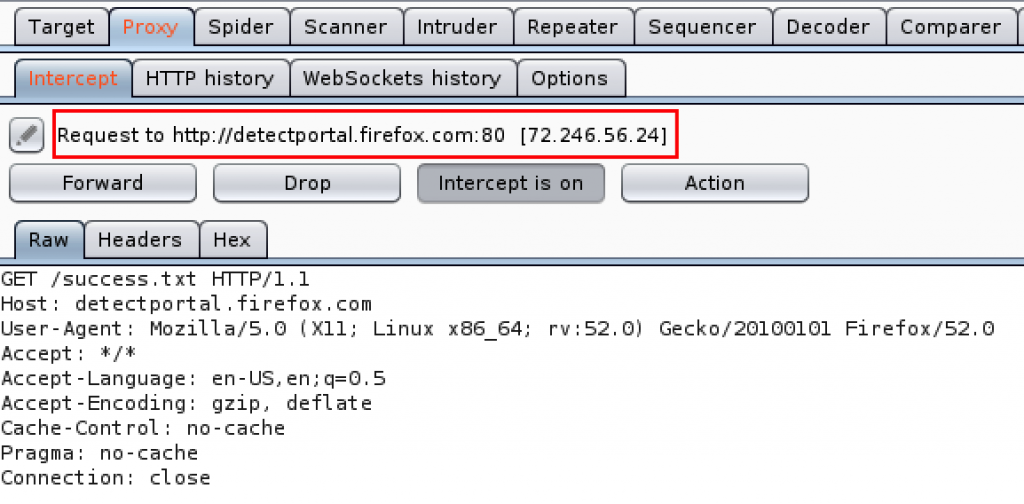
However, you may now be seeing a ton of requests like this:
Disable the detectportal.firefox.com requests
Seeing all those requests in Burp, much less thinking about all the noise they generate otherwise, is annoying. Because you probably won’t ever need to use a Captive Portal on your pentesting machine (a VM, in my case), you can completely disable Firefox’s attempts to detect them. Just browse to about:config and enter network.captive-portal-service.enabled. Double click it to change its value to “false” and you should be good to go.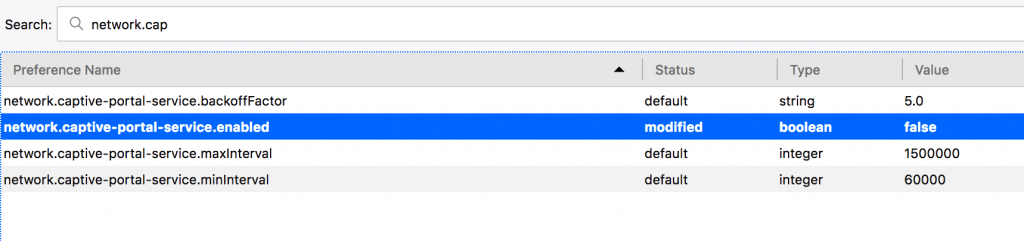
That’s all, folks!

Be First to Comment